How to Find Wireless Network Security Key in Windows 10
2-23-2021 12:30:43 AM
Problem:
You don't remember what your wireless security key is, but you wan to connect a new device up to your Wi-Fi. You do have a computer running Windows 10 that is already connected to the network.
Solution:
On your Windows 10 computer, press <Win><X> to bring up the Windows main menu:
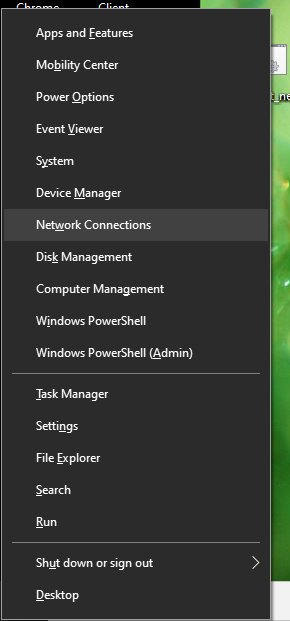
Click on Network Connections to bring up the network connections dialog:
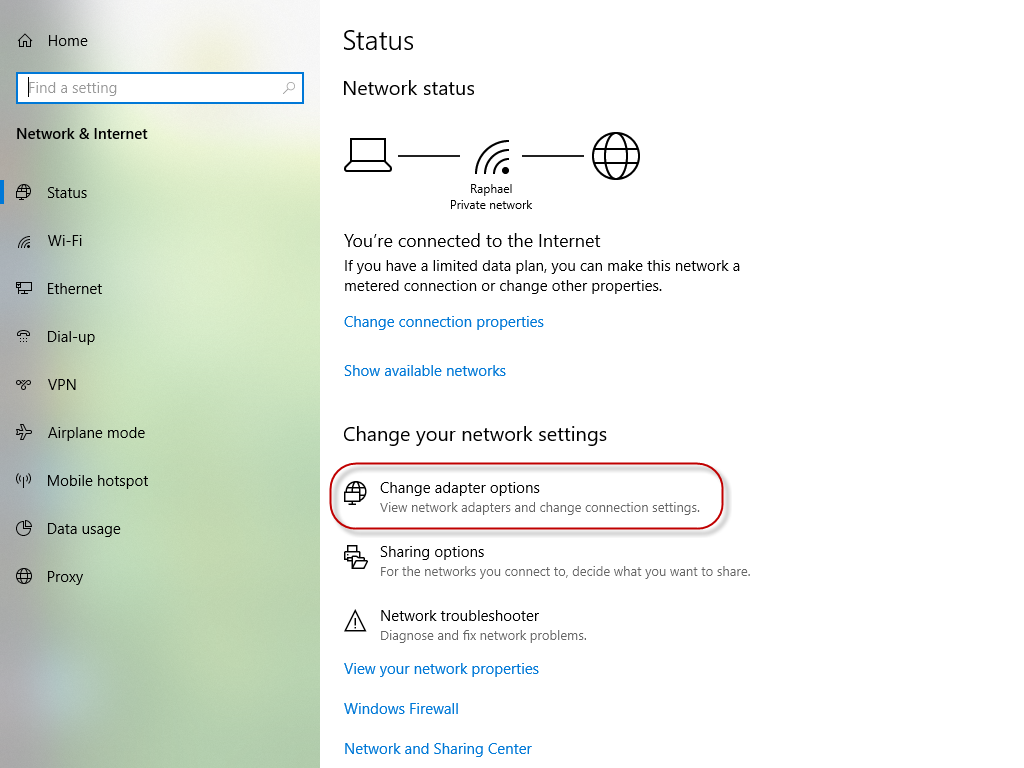
Click on Change adapter options to open the adapter options dialog:
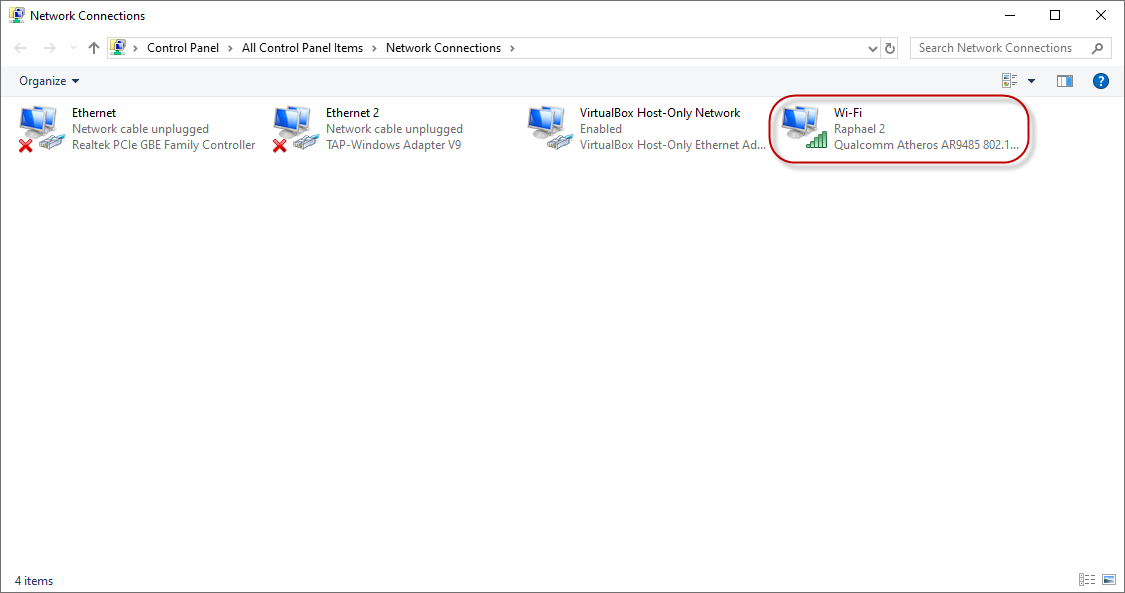
Double-click on the adapter that is your current Wi-Fi connection to open the Wi-Fi dialog:
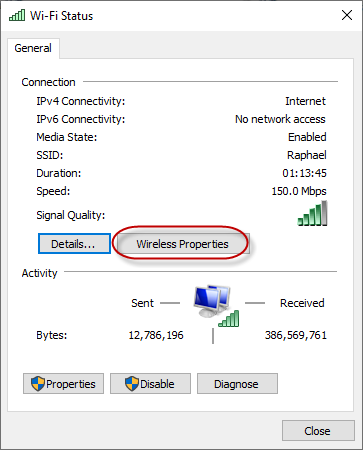
Click on Wireless Properties to open the wireless properties dialog:
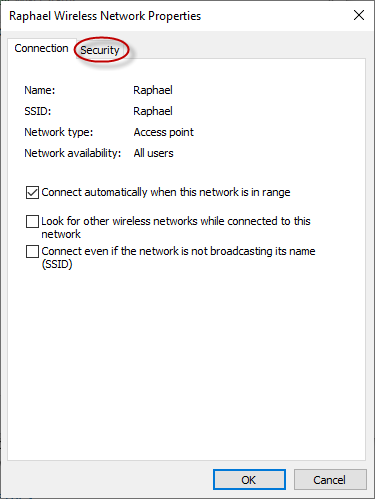
Click on the Security tab.
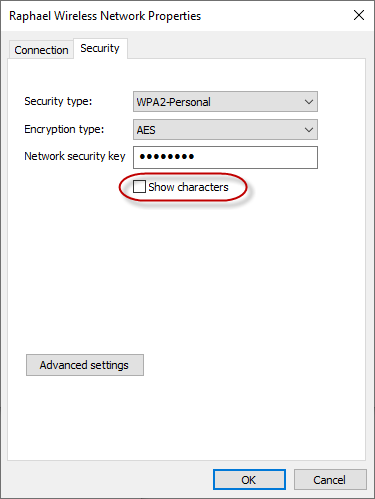
Click on the Show characters checkbox to real the network security key.
admin
Upgrade OpenCart to 3.0.6.0 Causes Admin Pages to be Blank
11-6-2020 2:29:17 AM
Problem:
Upgrade OpenCart from version 3.0.3.0 to version 3.0.6.0 and all pages come up blank including admin pages. Checking error log in the OpenCart root folder has the following error:
PHP Fatal error: Uncaught Error: Class 'TwigLoaderArrayLoader' not found in
Solution:
Follow the upgrade procedure as is with one exception. Do not replace (or restore if already overwritten) /(opencartroot)/system/library/template/twig.php
Edward Lemmers
New Version of Thunderbird
10-30-2020 2:43:22 PM
Thunderbird 78 is out. It has a number of important changes including a dark skin for night viewing, integrated tasks and calenders, and end-to-end encryption. For more information see https://www.thunderbird.net/en-US/thunderbird/78.0/whatsnew/?locale=en-US&version=78.4.0&channel=release&os=%OS%&buildid=%APPBUILDID%&oldversion=68.12.1
Edward Lemmers
MySQL error occurs after upgrading PHP/MySQL web app
3-17-2013 6:37:03 PM
Problem:
You upgrade a PHP/MySQL web app and you get the following error:
We are sorry, we not able to connect right now. Please try again later: SQLSTATE[HY000] [2000] mysqlnd cannot connect to MySQL 4.1+ using the old insecure authentication. Please use an administration tool to reset your password with the command SET PASSWORD = PASSWORD('your_existing_password'). This will store a new, and more secure, hash value in mysql.user. If this user is used in other scripts executed by PHP 5.2 or earlier you might need to remove the old-passwords flag from your my.cnf file
Analysis:
If the web app was installed when the server was running PHP 5.2 or earlier, or the web app was transferred from one CPanel/WHM server to another using the automatic transfer tool, the database user credintials were applied using the old 4.1 format.
Solution:
You can use SSH, then log into the MySQL console run the password update as described in the error message. As an alternative, you may also use the CPanel interface to delete, rescreate and re-apply the user to the database.
Ed Lemmers
Purchasing a Laptop - What Processor is Best?
9-17-2013 8:40:27 AM
As many savvy computers have become aware of, Intel markets their laptop processors under three different labels: Core i3, Core i5 and Core i7 which relate to different price range levers: economy, standard and premium. In Intel's desktop line, these model series relate directly to performance in terms of computing power. This is not necessarily true with laptops. Another consideration for laptop performance is battery life. As it turns out, there are Core i5 and Core i7 processors that currently being manufactured that have similar performance (or the Core i5 may actually run at a higher clock speed), but the Core i7 consumes half of the power of the Core i5. If you are planning on using your laptop mostly in situations where your are running it on battery power, then paying the premium for the Core i7 is well worth it. If on the other hand, you will not be traveling that often or you will generally have power available, you may prefer to have a slightly faster processor and to save a little money on the purchase as well.
Another aspect that is associated with the different levels of the Intel Core i series is the number of cores and threads each level has. For desktop processors, the Core i3 series has 2 physical cores and 4 threads, the Core i5 series has 4 physical cores and 4 threads (mostly), and the Core i7 series has 4 physical cores and 8 threads. This is not the case for Intel's mobile processors. In fact, most mobile Core i5 and Core i7 processors have only 2 physical cores and 4 threads for both series. But what does this mean in performance? The number of cores and threads becomes important as your computer is required to multitask. This can be extremely important for a programmer or developer who needs to run several operating systems in virtual machines simultaneously. But for the typical user, processor clock speed will have a greater impact on user experience.
It is typically easier to get higher clock speeds with Intel processors than AMD processors. Also, motherboards built with Intel chipsets seem to be better supported that other chipsets. But quad-core laptops running Intel processors tend to be high-end products and are harder to find. If you are on a budget and you want to run multiple OSes, and you need to use multi-threaded programs, than an AMD processor may be of better value to you. The AMD mobile processors are divide into different A series: A4, A6, A8, A10. The A4 series have 2 physical cores, the A6 series come with 2, 3 or 4 physical cores, and the A8 and A10 series all have 4 physical cores. The next 4 digits, i.e.. A8-5600K have a relationship to clock speed, but this relationship is not one-to-one. In fact sometimes higher numbers are used for slower clock speeds. Therefore, you will need to lookup the specifications of the CPU by the CPU model number in order to compare the performance between any to laptop computers. You can go to http://www.cpu-world.com for specific information about any CPU.
Ed Lemmers
What to do about Windows 8 that is pre-installed on your desktop or laptop computer?
9-24-2013 3:03:33 PM
I recently bought a new laptop, but as with most new laptops, it came with Windows 8 pre-installed. Windows 8 is designed only for tablets and cell phones which is great if you have a touch screen, you don't need to type a lot, and you won't be using multiple productivity programs, doing a lot of photo/image editing or using programmer's development tools. While true that most people use their computers for web browsing, emails and social media, there still is the rest of us that still need to get work done.
Knowing how easy it is to install Linux Mint along side Windows, I decided to not let which version of Windows that was pre-installed on the laptops determine which laptop I was going to buy. I would have Windows 8 for testing, and I would do most of my work in Linux Mint which I find to be very useful, powerful and efficient. So I popped my Linux Mint Cinnamon DVD into the drive, booted the computer and proceeded to install dedicated half of my hard drive to Linux Mint and half to Windows 8. The Install ran very smoothly resizing the partitions and install Linux Mint. I rebooted and no GRUB boot loader came up. Windows 8 starting loading like nothing had ever happened, except the amount of available space was now cut in half. Two more days of research and trying this and that went by before I had both Linux Mint and Windows installed on my computer. (As a web developer, Windows running natively on my computer is still necessary because most people still use it and my websites need to be tested to work properly in that environment.) So to save you the horrors of my experience, I will briefly describe three options to setup your new desktop or laptop with a desktop/laptop operating system/environment and I will describe some of the possible unforeseen challenges you may come into. If you have any questions, please feel free to call into the Ray Carr show on Tuesday mornings between 7:00 and 9:00 AM Tuesday mornings.
Option 1: Configure Windows 8 to behave more like Windows 7.
You can change your startup screen to the desktop, streamline menus, and install the glass areo look. Avram Piltch has already put together a detailed blog on how to do this: http://blog.laptopmag.com/make-windows-8-like-windows-7
Option 2: Downgrade to Windows 7.
This is not as easy as it sounds. The licensing of Windows is now handled in the BIOS of the computer. This is done with SLIC (system and logistics integration capability) which allows computer manufactures to easily install Windows on their computers with the need to have different key codes for each machine. The latest version of SLIC can specify that the computer is licensed for Windows 8, but not Windows 7. Thus if you want to downgrade to Windows 7, you will either need to purchase Windows 7 or use a SLIC emulator to get a copy of Windows 7 to activate automatically.
Option 3: Install Linux Mint.
Normally, Linux Mint installs along side Windows 8 without a problem. But computer manufactures may use exotic partitioning schemes to allow for system restore capability and for hard drive larger than 2 TB. This was the case with an HP laptop I setup. The Linux Mint installation went fine, resizing the Windows 8 partition, and installing Linux Mint on the free space of the hard drive. The installation then proceeded to write GRUB to one of the many hidden partitions, thus rebooting only brought up the Windows launcher menu. Deleting all of the partitions and starting from scratch allowed Windows 7 to install fine, but Linux Mint could not detect its presence due to the hard drive being setup with GPT tables. This fix was to use gParted to setup the drive for msdos partitions and start all over with a Windows 7 install to have of the drive, then a Linux Mint install to the other half of the drive.
Ed Lemmers
Subject - Latest Pishing Scam
10-1-2019 4:51:35 PM
Got email today. Email address was spoofed as PayPal <service@paypal.com> Subject is For payment you have a little more than two days (exactly 50 hours). This email appears real but fake. Nobody uses Internet Explorer on this computer and nobody views porn on it. If you get the email below, just delete it.
BITCOIN Wallet 17miid2m38nshNEV7xhhgrXbuPzuz9p2rc
|
I have very bad news for you
22 / 05 / 2019 - on this day I hacked your operating system and got full access to your account .
It is useless to change the password, my malware intercepts it every time.
How it was:
In the software of the router to which you were connected that day, there was a vulnerability.
I first hacked this router and placed my malicious code on it.
When you entered in the Internet, my trojan was injected into explorer.exe on the operating system of your device.
After that, I made a full dump of your disk (I have all your address book, history of viewing sites, all files, phone numbers and addresses of all your contacts).
A month ago, I wanted to lock your device and ask for a small amount of money to unlock.
But I looked at the sites that you regularly visit, and came to the big delight of your favorite resources.
I'm talking about sites for adults.
I want to say - you are a big, big pervert. You have unbridled fantasy!!!
After that, an idea came to my mind.
I made a screenshot of the intimate website where you have fun (you know what it is about, right?).
After that, I made a screenshot of your joys (using the camera of your device) and joined all together.
It turned out beautifully, do not doubt.
I am strongly belive that you would not like to show these pictures to your relatives, friends or colleagues.
I think $ 718 is a very small amount for my silence.
Besides, I spent a lot of time on you!
I accept money only in Bitcoins.
My BTC wallet: 17miid2m38nshNEV7xhhgrXbuPzuz9p2rc
You do not know how to replenish a Bitcoin wallet?
In any search engine write "how to send money to btc wallet".
It's easier than send money to a credit card!
For payment you have a little more than two days (exactly 50 hours).
Do not worry, the timer will start at the moment when you open this letter. Yes, yes .. it has already started!
After payment, my virus and dirty photos with you self-destruct automatically.
Narrative, if I do not receive the specified amount from you, then your device will be blocked, and all your contacts will receive a photos with your "joys".
I want you to be prudent.
- Do not try to find and destroy my virus! (All your data is already uploaded to a remote server)
- Do not try to contact me (this is not feasible, I sent you an email from your account)
- Various security services will not help you; formatting a disk or destroying a device will not help either, since your data is already on a remote server.
P.S. I guarantee you that I will not disturb you again after payment, as you are not my single victim.
This is a hacker code of honor.
From now on, I advise you to use good antiviruses and update them regularly (several times a day)!
Don't be mad at me, everyone has their own work. |
Edward Lemmers
MySQL error occurs after upgrading PHP/MySQL web app
8-8-2019 5:47:53 PM
Problem:
You upgrade a PHP/MySQL web app and you get the following error:
We are sorry, we not able to connect right now. Please try again later: SQLSTATE[HY000] [2000] mysqlnd cannot connect to MySQL 4.1+ using the old insecure authentication. Please use an administration tool to reset your password with the command SET PASSWORD = PASSWORD('your_existing_password'). This will store a new, and more secure, hash value in mysql.user. If this user is used in other scripts executed by PHP 5.2 or earlier you might need to remove the old-passwords flag from your my.cnf file
Analysis:
If the web app was installed when the server was running PHP 5.2 or earlier, or the web app was transferred from one CPanel/WHM server to another using the automatic transfer tool, the database user credintials were applied using the old 4.1 format.
Solution:
You can use SSH, then log into the MySQL console run the password update as described in the error message. As an alternative, you may also use the CPanel interface to delete, rescreate and re-apply the user to the database.
Ed Lemmers
Purchasing a Laptop - What Processor is Best?
8-8-2019 5:26:14 PM
As many savvy computers have become aware of, Intel markets their laptop processors under three different labels: Core i3, Core i5 and Core i7 which relate to different price range levers: economy, standard and premium. In Intel's desktop line, these model series relate directly to performance in terms of computing power. This is not necessarily true with laptops. Another consideration for laptop performance is battery life. As it turns out, there are Core i5 and Core i7 processors that currently being manufactured that have similar performance (or the Core i5 may actually run at a higher clock speed), but the Core i7 consumes half of the power of the Core i5. If you are planning on using your laptop mostly in situations where your are running it on battery power, then paying the premium for the Core i7 is well worth it. If on the other hand, you will not be traveling that often or you will generally have power available, you may prefer to have a slightly faster processor and to save a little money on the purchase as well.
Another aspect that is associated with the different levels of the Intel Core i series is the number of cores and threads each level has. For desktop processors, the Core i3 series has 2 physical cores and 4 threads, the Core i5 series has 4 physical cores and 4 threads (mostly), and the Core i7 series has 4 physical cores and 8 threads. This is not the case for Intel's mobile processors. In fact, most mobile Core i5 and Core i7 processors have only 2 physical cores and 4 threads for both series. But what does this mean in performance? The number of cores and threads becomes important as your computer is required to multitask. This can be extremely important for a programmer or developer who needs to run several operating systems in virtual machines simultaneously. But for the typical user, processor clock speed will have a greater impact on user experience.
It is typically easier to get higher clock speeds with Intel processors than AMD processors. Also, motherboards built with Intel chipsets seem to be better supported that other chipsets. But quad-core laptops running Intel processors tend to be high-end products and are harder to find. If you are on a budget and you want to run multiple OSes, and you need to use multi-threaded programs, than an AMD processor may be of better value to you. The AMD mobile processors are divide into different A series: A4, A6, A8, A10. The A4 series have 2 physical cores, the A6 series come with 2, 3 or 4 physical cores, and the A8 and A10 series all have 4 physical cores. The next 4 digits, i.e.. A8-5600K have a relationship to clock speed, but this relationship is not one-to-one. In fact sometimes higher numbers are used for slower clock speeds. Therefore, you will need to lookup the specifications of the CPU by the CPU model number in order to compare the performance between any to laptop computers. You can go to http://www.cpu-world.com for specific information about any CPU.
Ed Lemmers